Introduction
In previous posts, we’ve explored how to set up Cloud PKI and implement certificate-based authentication in Entra ID across different platforms, including Windows, macOS, and Android. Each of these environments has unique steps and considerations for deploying certificates and securing access to corporate resources.
Now, it’s time to focus on iOS devices. In this post, we’ll walk you through the process of deploying root and SCEP certificates on iOS using Microsoft Intune. We’ll break down the steps and highlight how these configurations affect both security and user experience, ensuring a seamless integration for iOS users in your organization.
Trusted Certificate Deployment for iOS
Prerequisites:
- iOS devices running iOS 14.0 or later.
- Access to Microsoft Intune with required permissions.
- A trusted CA certificate in .cer or .pem format.
- Microsoft Authenticator for Office apps.
Steps:
Log into Microsoft Endpoint Manager Admin Center:
- Access the admin center here and sign in with your credentials.
Navigate to Devices:
- Go to Devices in the left-hand menu.
- Select iOS/iPadOS under By platform.
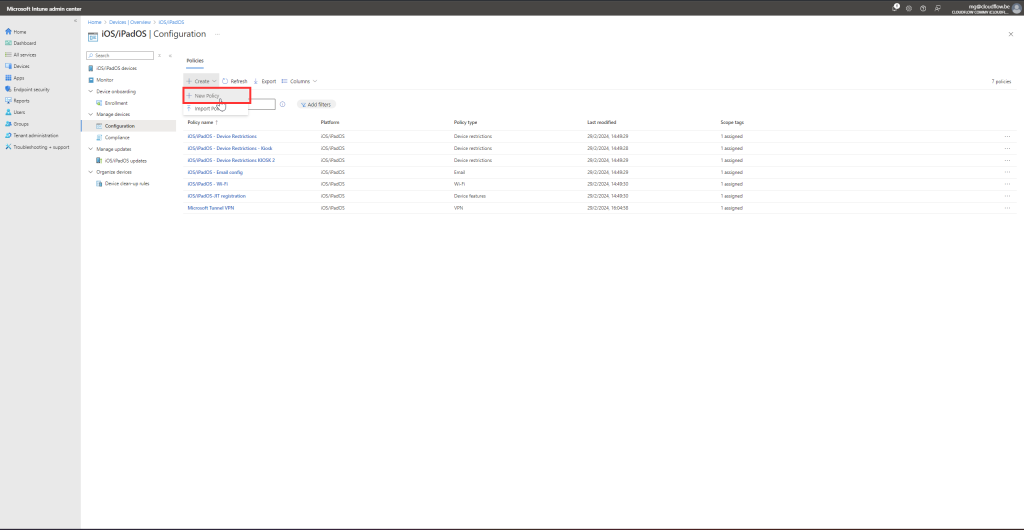
Create a New Profile:
- Click + Create profile and choose iOS/iPadOS as the platform.
- Select Trusted Certificate for the profile type.
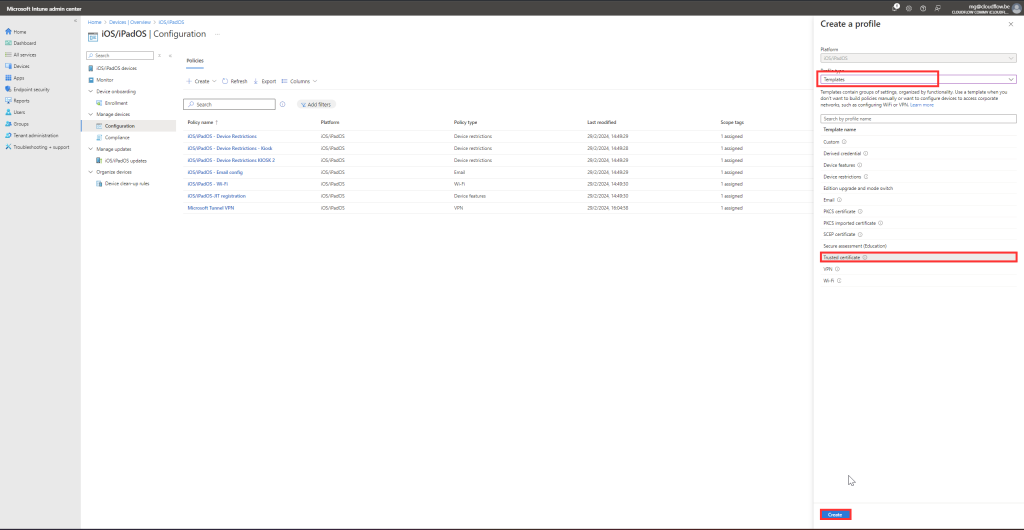
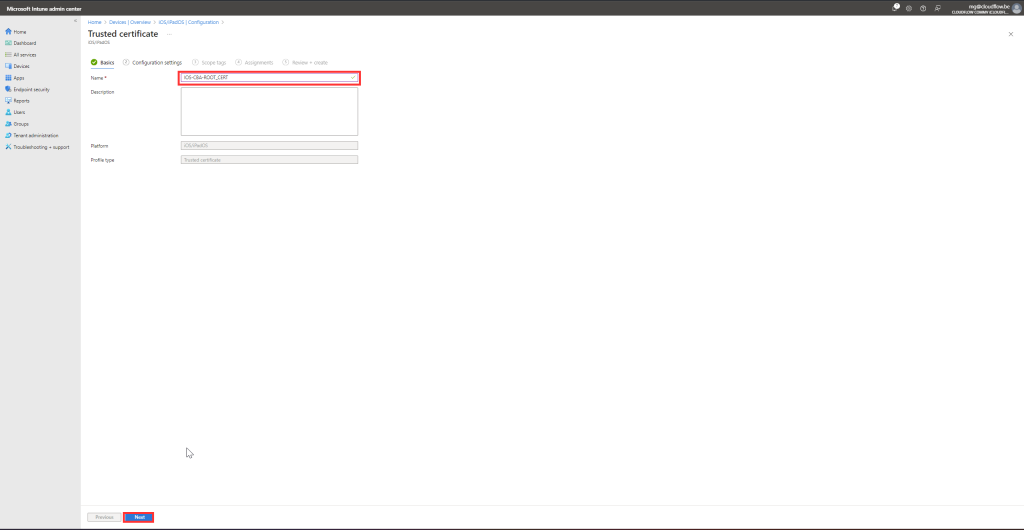
Configure the Profile:
- Provide a Name and Description.
- Under Settings, select Trusted Certificate, then upload the .cer or .pem file.
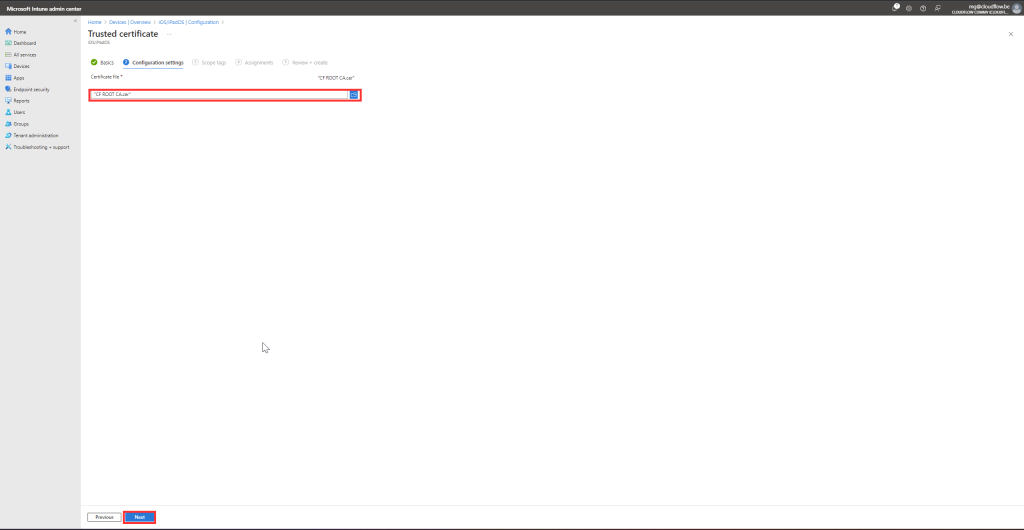
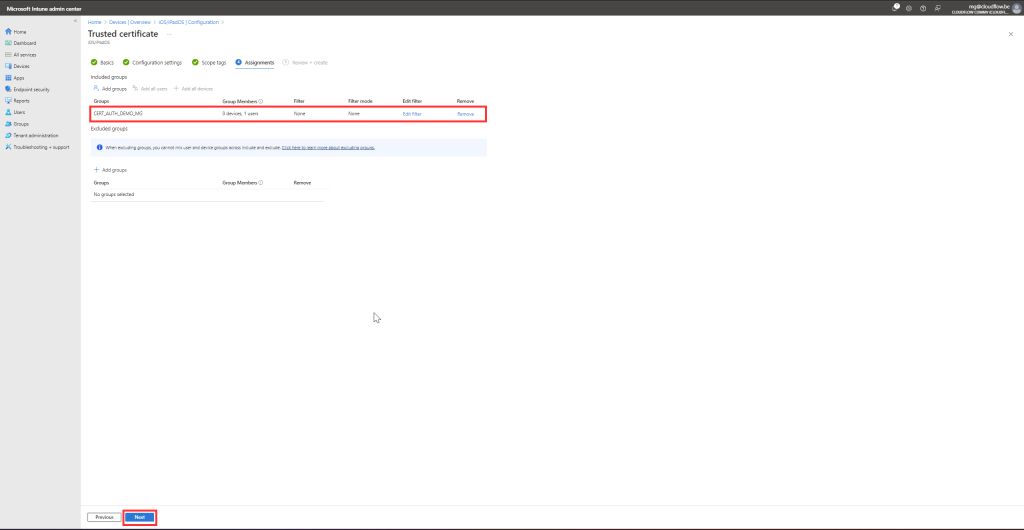
Assign the Profile:
- Click Next.
- Assign the profile to relevant device groups.
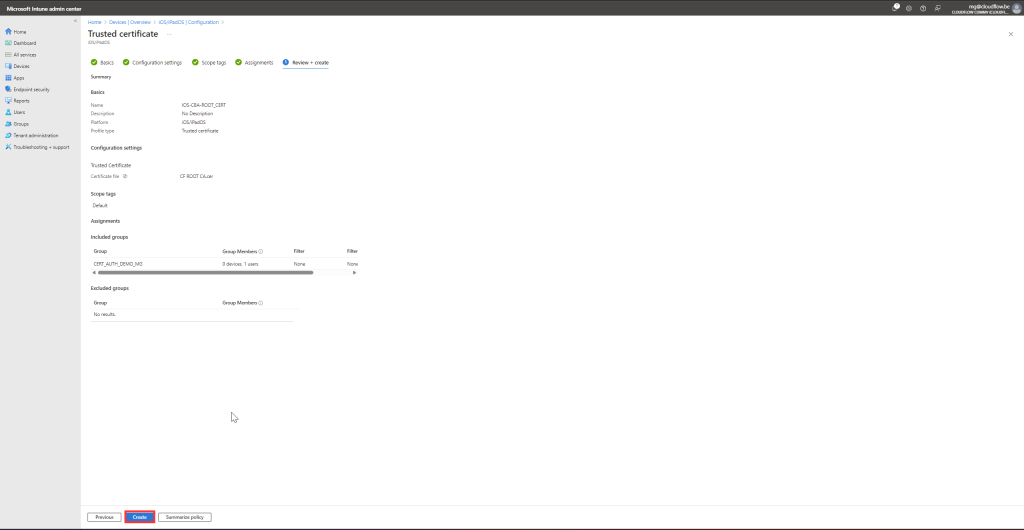
Review and Create:
- Review your settings and click Create.
Sync the Device:
- On the iOS device, open the Company Portal app and navigate to Devices.
- Select the device and click Check status to initiate a sync.
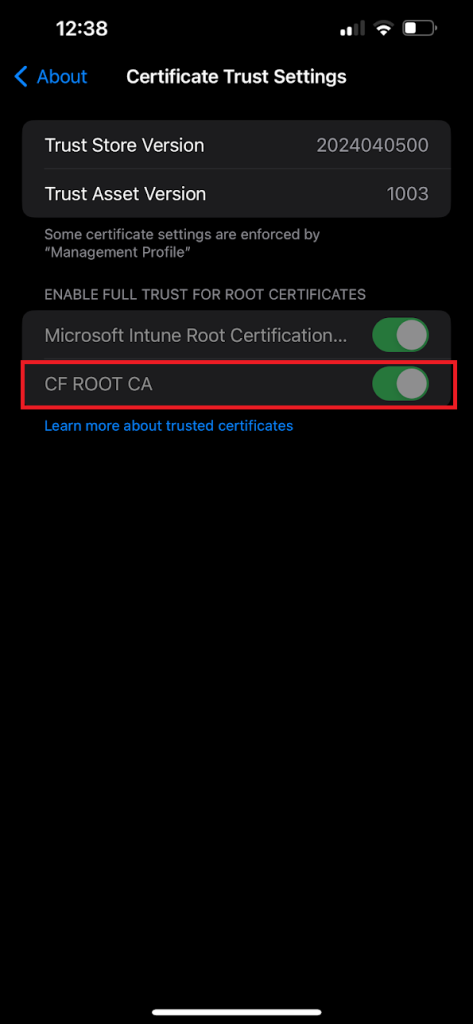
Verify Installation:
Follow these steps to find the version of the Trust Store installed on your iOS and iPadOS device:
- Tap Settings > General > About
- Scroll to the bottom of the list
- Tap Certificate Trust Settings
SCEP Certificate Deployment for iOS
Prerequisites:
- Access to Microsoft Intune with the necessary permissions.
- SCEP server URL and credentials.
- iOS devices enrolled in Intune.
Steps:
Log into Microsoft Endpoint Manager Admin Center:
- Log into the admin center and sign in using your credentials.
Navigate to Devices:
- Go to Devices and select iOS/iPadOS under By platform.
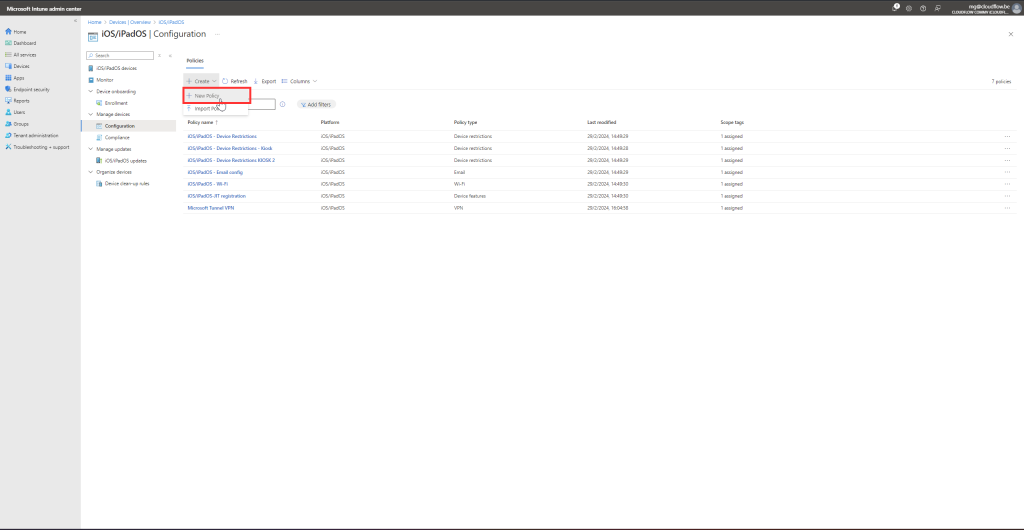
Create a New Profile:
- Click + Create profile and select iOS/iPadOS as the platform.
- Choose SCEP Certificate for the profile type.
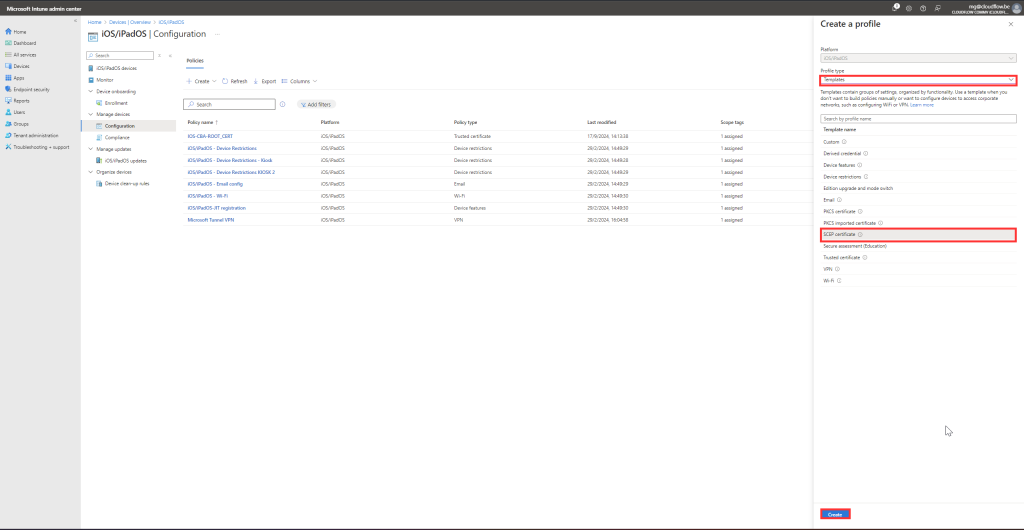
Configure SCEP Settings:
- Provide a Name and Description.
- Under Settings, select SCEP certificate.
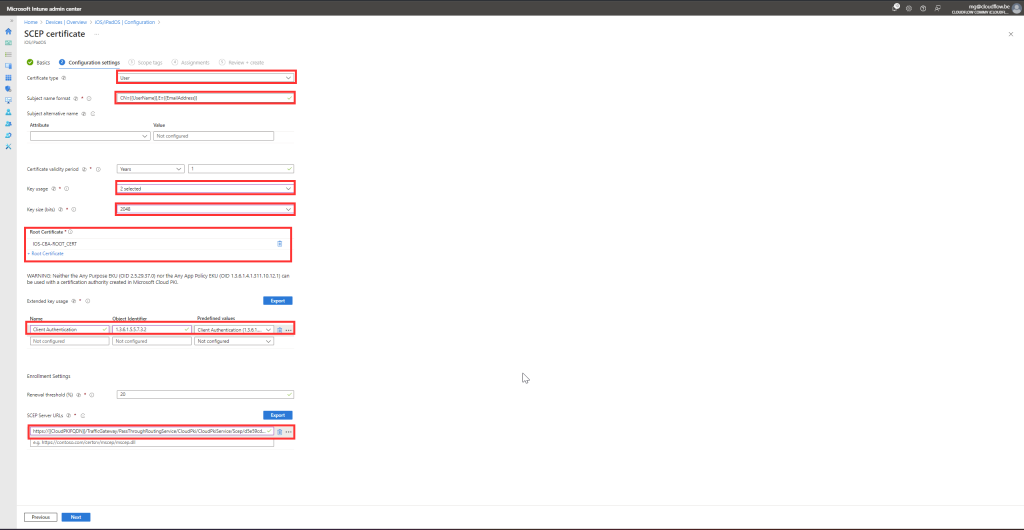
- Fill out the fields:
- Name: Enter a name for the SCEP certificate.
- Certificate type: Choose User.
- Subject name format: Use a format like
CN={{UserPrincipalName}}. - SCEP server URL: Provide your server’s URL.
- Key Usage: Select Digital Signature and Key Encipherment.
- Key Size: Choose 2048 bits.
Assign the Profile:
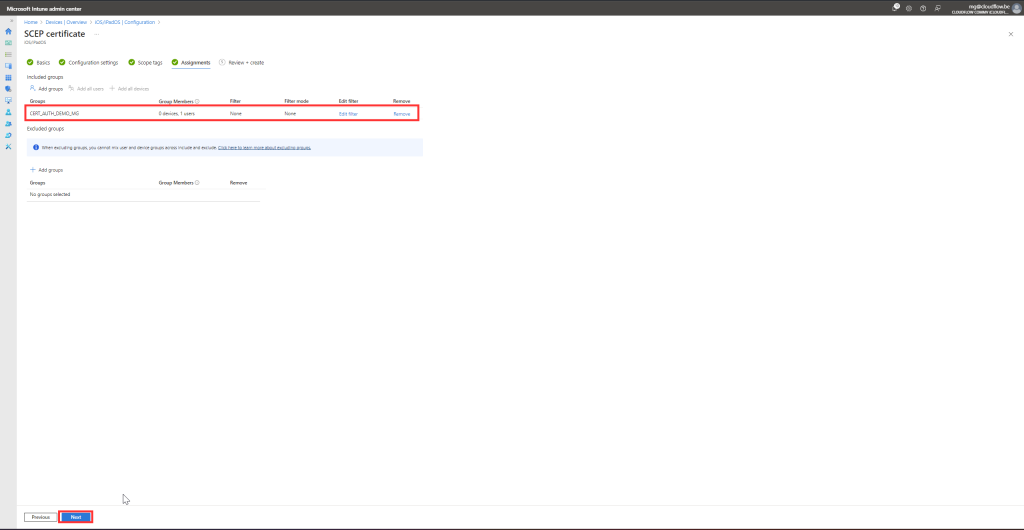
- Click Next and assign the profile to the appropriate groups of iOS devices.
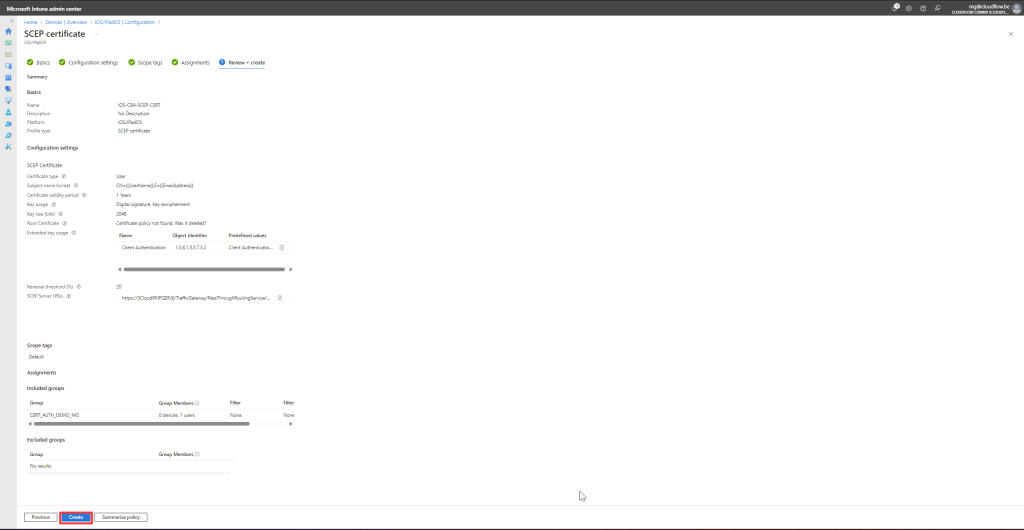
Review and Create:
- Review the settings and click Create.
Sync the Device:
- On the iOS device, open the Company Portal app, go to Devices, and click Check status to initiate a sync.
Verify Installation:
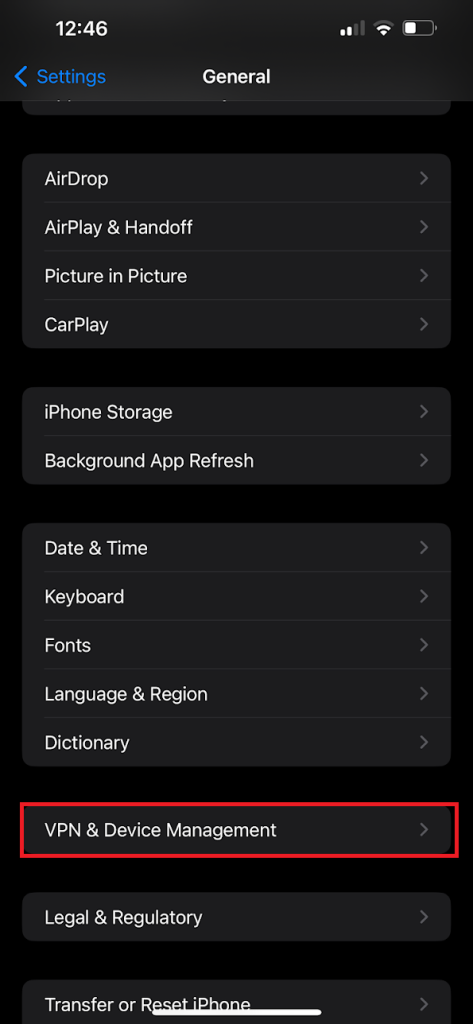
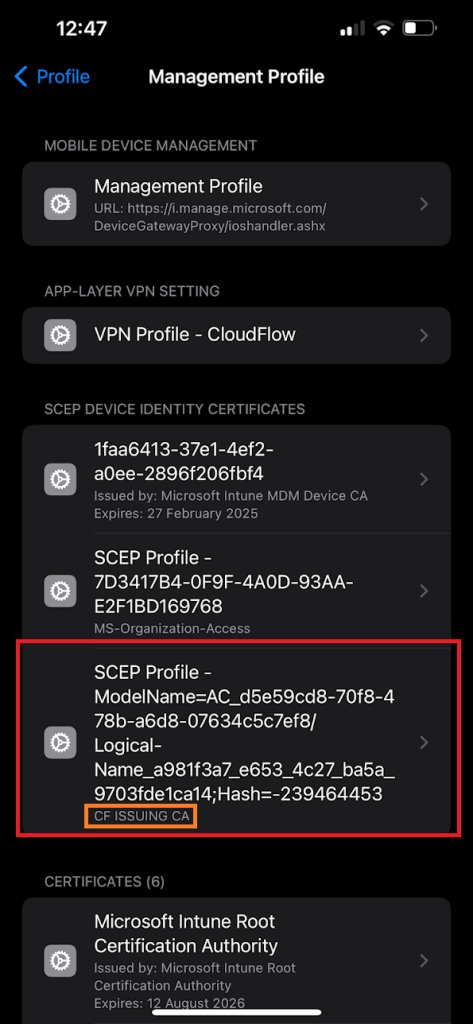
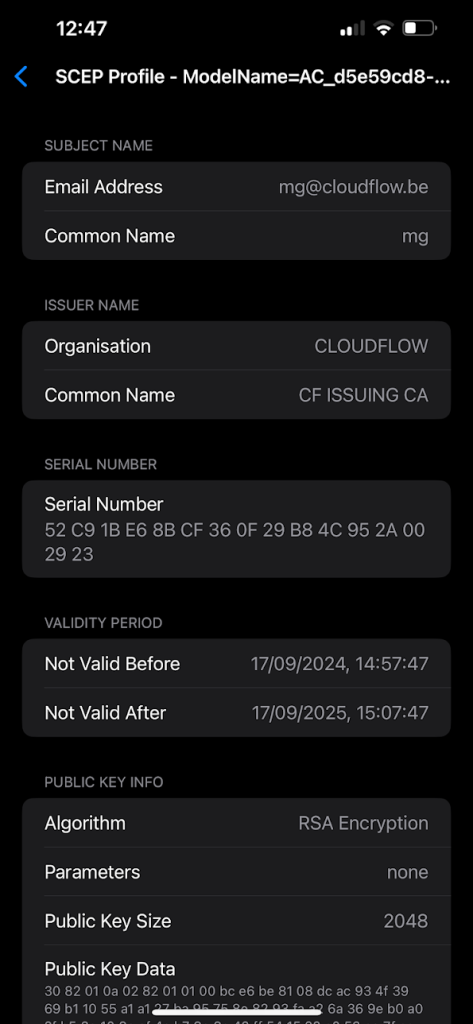
On an iPhone, SCEP (Simple Certificate Enrollment Protocol) certificates can typically be found in the Profiles & Device Management section of the settings. To locate them, follow these steps:
- Open Settings on the iPhone.
- Scroll down and tap on General.
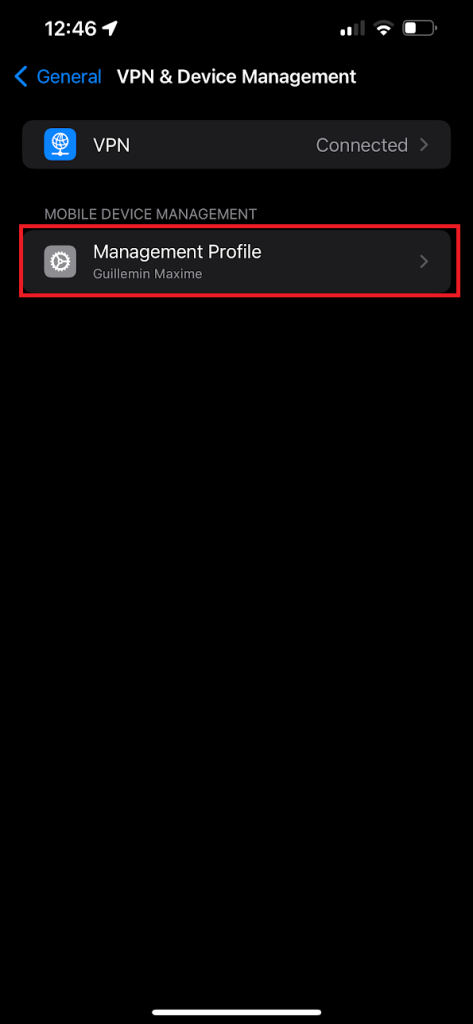
- Scroll down and select VPN & Device Management (or Profiles & Device Management, depending on the iOS version).
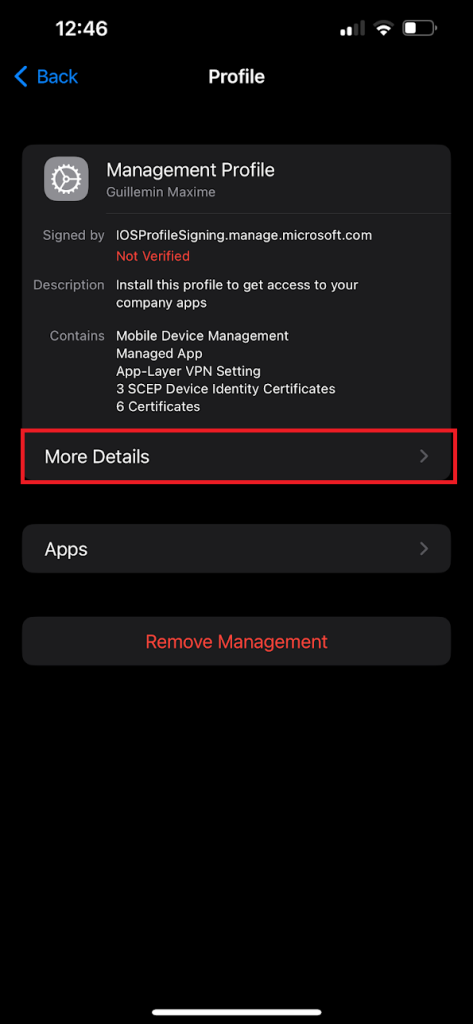
- If there is a profile that contains a SCEP certificate, it will be listed under Configuration Profiles. Tap on the profile to view its details.
- You should see the SCEP certificate under the profile details if it’s been installed.
User Experience
Supported Applications and Browsers:
Microsoft Entra ID supports certificate-based authentication (CBA) for apps like Outlook, Teams, OneDrive, and Office Mobile. Safari is the only
Important Note: For office Application you will need the Microsoft Authentication App!
Safari Experience
It is important to note that Safari is the only officially supported browser for this platform. This means that you won’t have the option to use other popular browsers such as Microsoft Edge, Google Chrome, or Firefox for this particular experience.
Unsupported Browsers Experience
In this video, I show a failed login attempt using certificate-based authentication (CBA) for Entra ID on iOS with Chrome. The reason it fails is that Chrome, like other third-party browsers on iOS, can’t access the device’s certificate store due to Apple’s security restrictions. This means it can’t use the required client certificates for login. Safari, on the other hand, has full access and handles CBA without issues. To avoid this problem, users should stick to Safari or apps that natively support certificates for a smooth login experience.
Office 365 Apps experience
In this video, I show a login attempt to an Office 365 app using certificate-based authentication (CBA). To complete the login, the app needs to open the Microsoft Authenticator app to access the certificate stored on the device. The Office 365 app itself can’t directly access the certificate, so it relies on Authenticator to handle it. Once the certificate is validated through the Authenticator app, the login goes through smoothly. This shows how the Microsoft Authenticator app is essential for securely handling certificate-based logins in Office 365 apps on iOS.
Conclusion
Deploying root and SCEP certificates on iOS devices using Microsoft Intune is a powerful way to enhance security through certificate-based authentication. This method ensures that only authorized devices can access sensitive corporate resources, providing a significant security advantage. However, it’s important to weigh both the benefits and the limitations.
Pros of Certificate-Based Authentication:
- Stronger Security: Certificates provide an extra layer of protection, reducing vulnerabilities to phishing and password-based attacks.
- Integration with Microsoft Ecosystem: It works seamlessly with apps like Outlook, Teams, and OneDrive, ensuring a smooth workflow once configured.
- Minimal User Disruption: After setup, the process runs in the background, making it simple for end users to access their apps securely.
Cons of Certificate-Based Authentication:
- Browser Restrictions: On iOS, Safari is the only browser that fully supports certificate-based authentication, which may frustrate users who prefer alternatives like Chrome or Edge.
- Dependency on Microsoft Authenticator: Office apps require the Microsoft Authenticator app to manage certificates, adding an extra step to the login process..
Now that you’ve explored the process of deploying certificate-based authentication on iOS devices, you should have a solid understanding of how it functions and the steps involved. If you haven’t already, I recommend checking out my previous posts, including the macOS post for Apple-specific details and the Android post for BYOD scenarios. To dive deeper into the setup of Cloud PKI, don’t forget to review Part 1 and Part 2 of this series, and explore Part 4 to learn how Conditional Access policies can enhance your certificate-based authentication strategy.
In upcoming content, I’ll be documenting 802.1X authentication using Microsoft Intune Cloud PKI, which offers another powerful way to secure network access. If this is something you’d be interested in, let me know, and stay tuned for more!






Any chance you could re-capture the screenshots of the admin center so they dont appear so tiny in this blog?
Hey Robb
I will have a look at this week if i can make the screenshots bigger 😉
kind regards
maxime
I have read the entire series, and it has helped me tremendously in my set up. Can’t thank you enough for the great presentation and write up. Keep up the good work.
Hey Prakash
Thanks for the kind words and glad to help.
Can you please clarify this?
Supported Applications and Browsers:
Microsoft Entra ID supports certificate-based authentication (CBA) for apps like Outlook, Teams, OneDrive, and Office Mobile. Safari is the only
Important Note: For office Application you will need the Microsoft Authentication App!
// What are you referring to as “office application?”