What is it ?
It is a simplified version of the original Autopilot, with no need to waste time extracting hardware hashes on existing devices and enrolling them in the Intune portal. Simply create one or multiple Windows Autopilot Device Preparation (WADP) policies depending on your use case.
How does it work
Traditional Autopilot worked with hardware hashes, allowing you to assign an Autopilot profile using these hashes. But with WADP, as stated above, you don’t need them anymore. Hooray! Now, I can hear you thinking, “How does it know what to do during the OOBE?” Instead of relying on the hardware hash, it uses the user Work school account. Once you log in to your M365 account, and that user is scoped to the desired WADP profile, it will use the configuration linked to that WADP profile. Be aware that it only supports user-driven Entra ID joined devices, and if the device is enrolled in the original Autopilot, it will always take precedence over WADP. Now, let’s get started on how to set it up.
How to set it up
Set up Windows automatic Intune enrolment
Go to https://intune.microsoft.com > Devices > Windows > Windows Enrolment > Automatic Enrolment
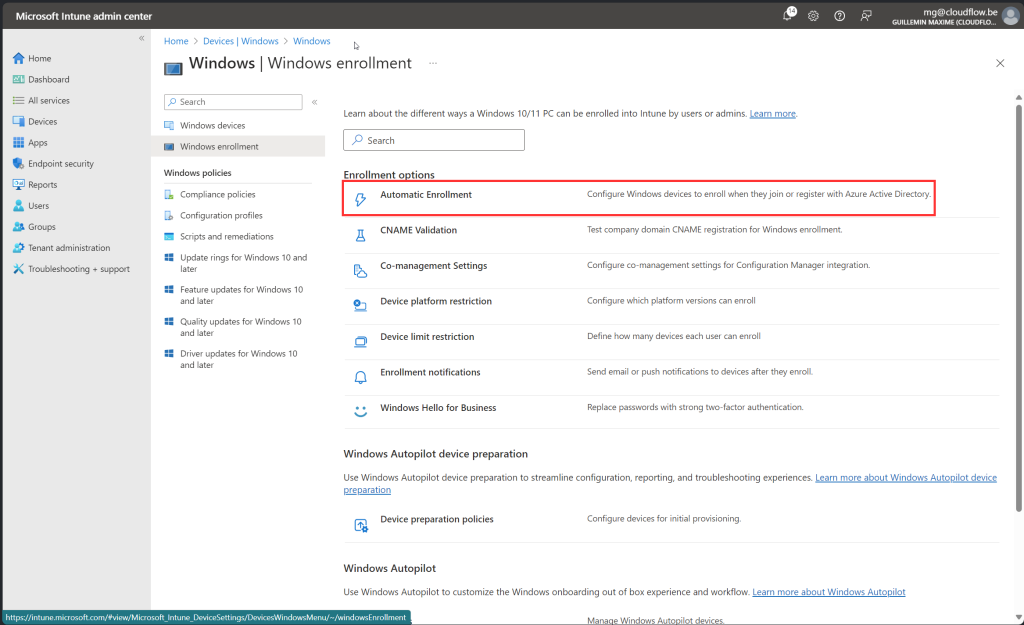
Here you have the option to use a User security group or allow all users to enrol
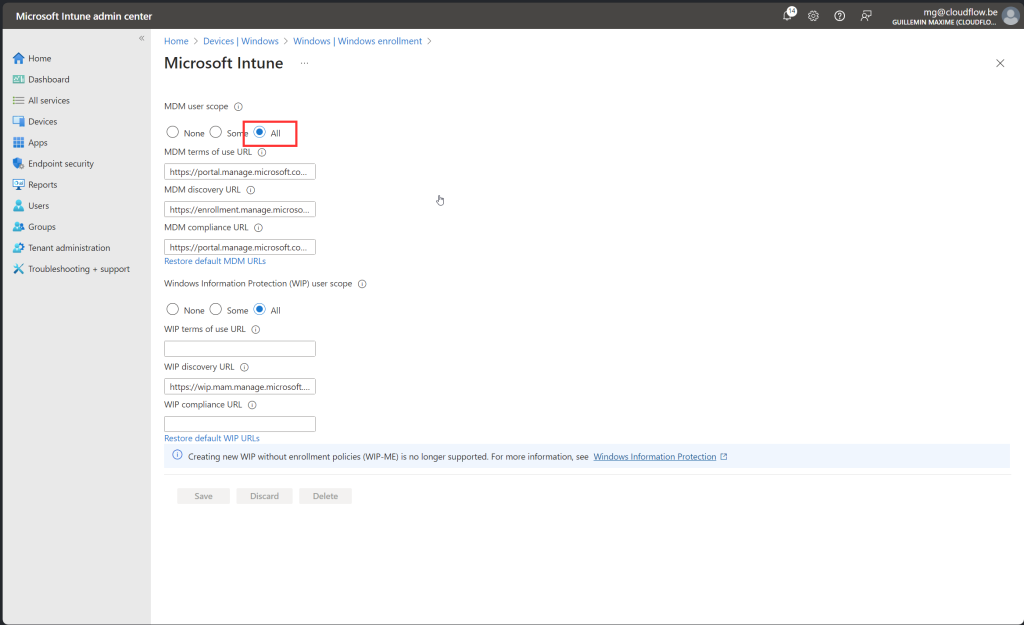
Allow users to join devices to Microsoft Entra ID
Go to https://portal.azure.com -> EntraID > Devices > Device Settings
Again you have the option to allow all users or Select a User security group
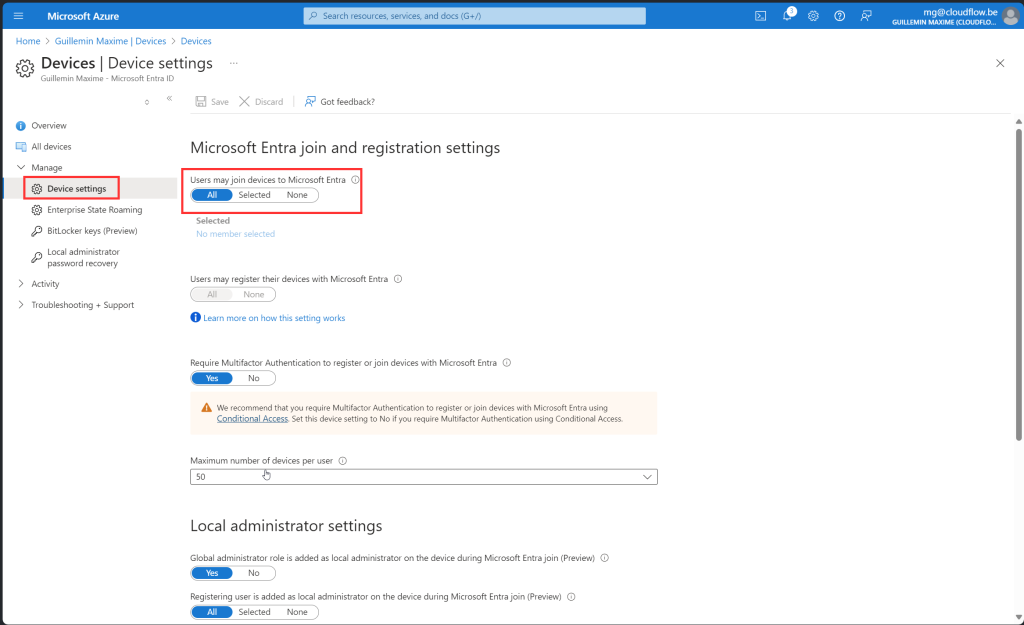
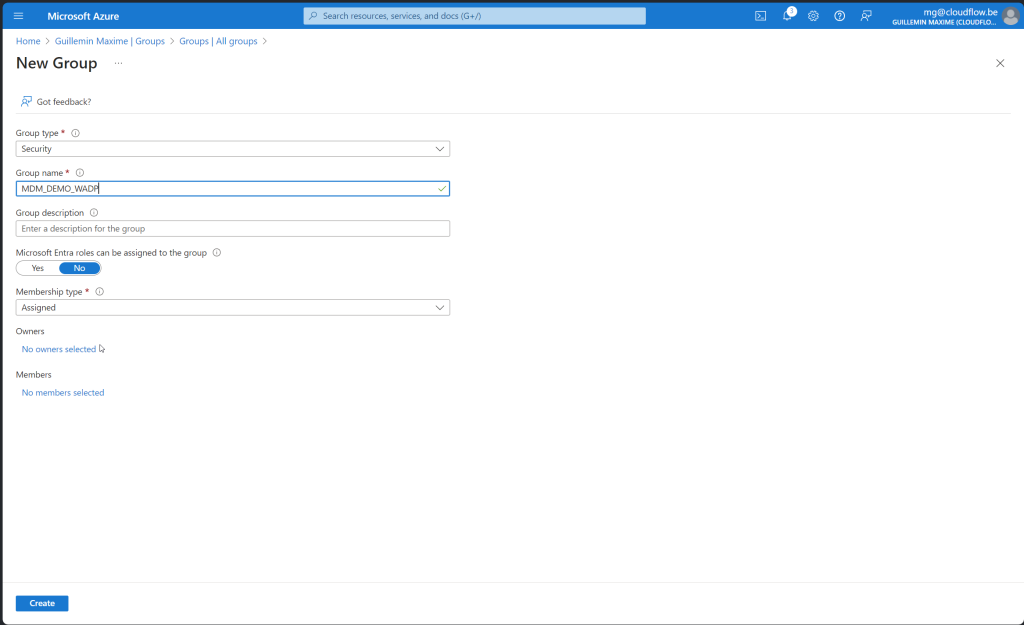
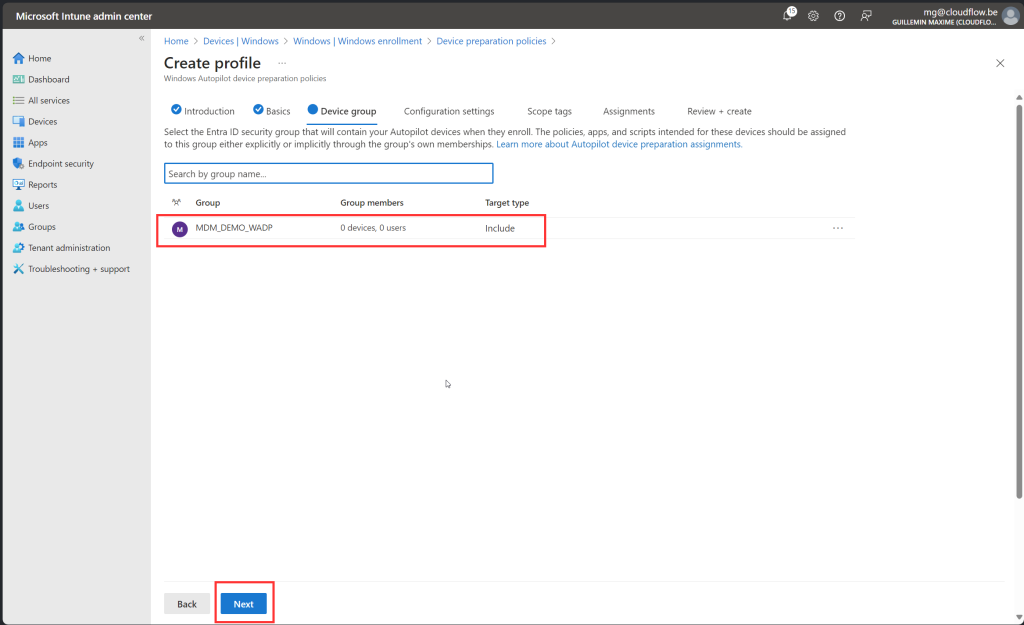
Create a device group
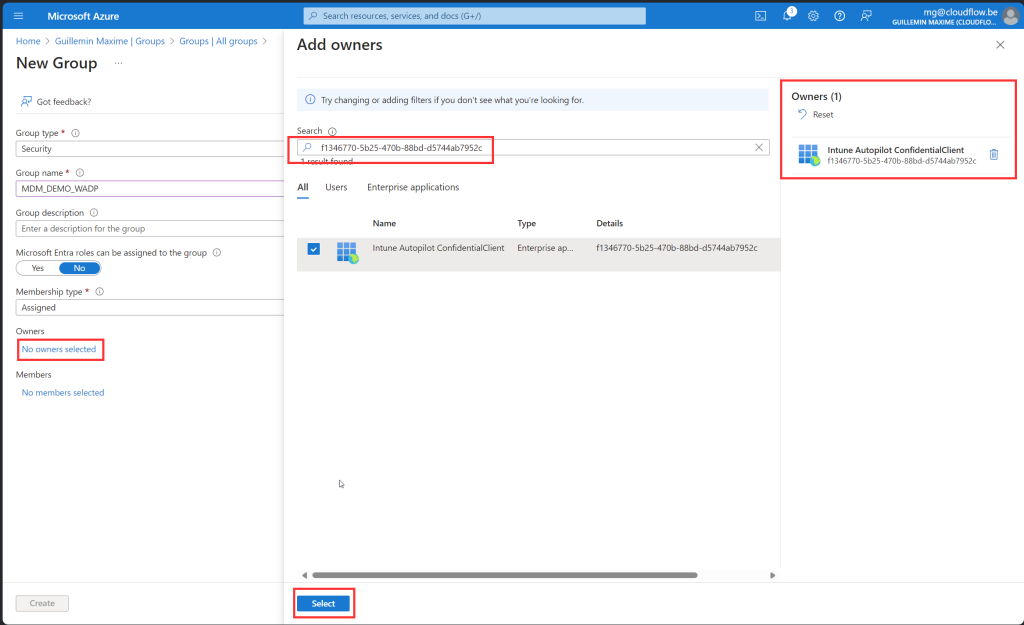
Before we create the group, here is some important information about this group. When creating this group, you need to make it an Assigned Security Group and add an owner to the group with the following ID: f1346770-5b25-470b-88bd-d5744ab7952c. It is possible that the name of the enterprise app is different from what appears in my screenshots. Do not manually add any devices to the device group created in this step by selecting the “No members selected” link under Members. Devices are automatically added to this device group during the Windows Autopilot device preparation deployment.
If you don’t find this enterprise app, don’t worry. You can create it using PowerShell. For more information, please read the page Windows Autopilot device preparation user-driven Microsoft Entra join – Step 3 of 7 – Create a device group | Microsoft Learn
Go to https://portal.azure.com -> EntraID > Groups > New Group
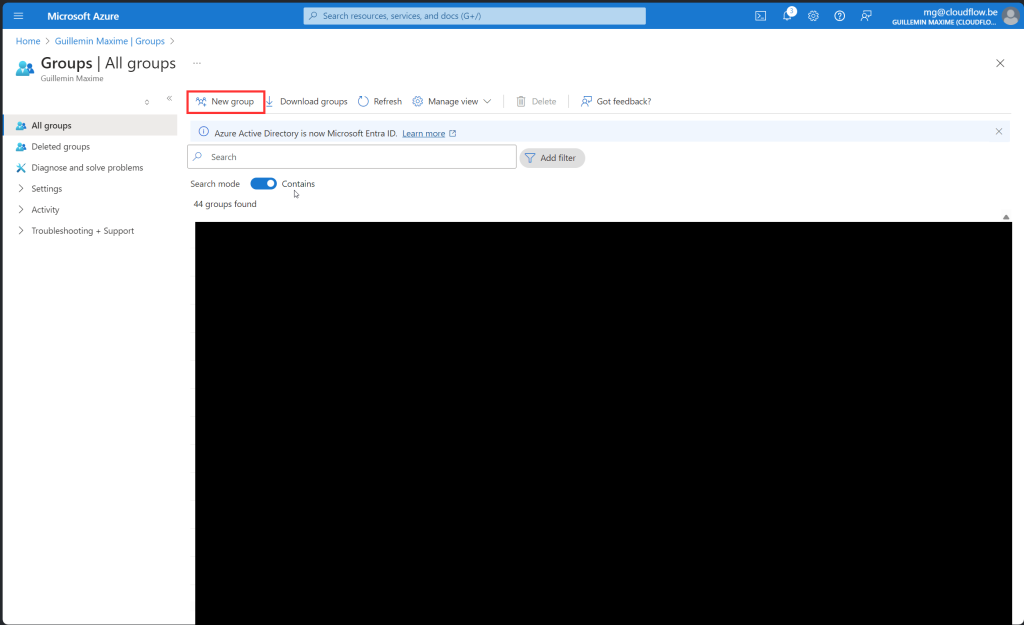
Create a user group
Go to https://portal.azure.com -> EntraID > Groups > New Group
This security group can be a dynamic or an assigned user group. For this demo, I’ll be using an assigned user group. This group will be used to assign the WADP policy to the user.
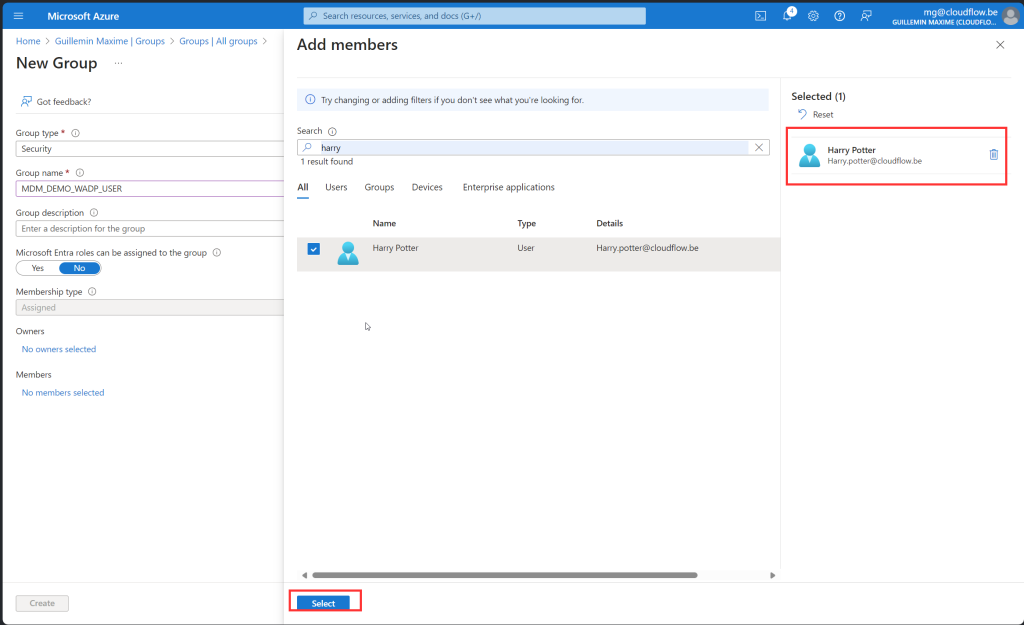
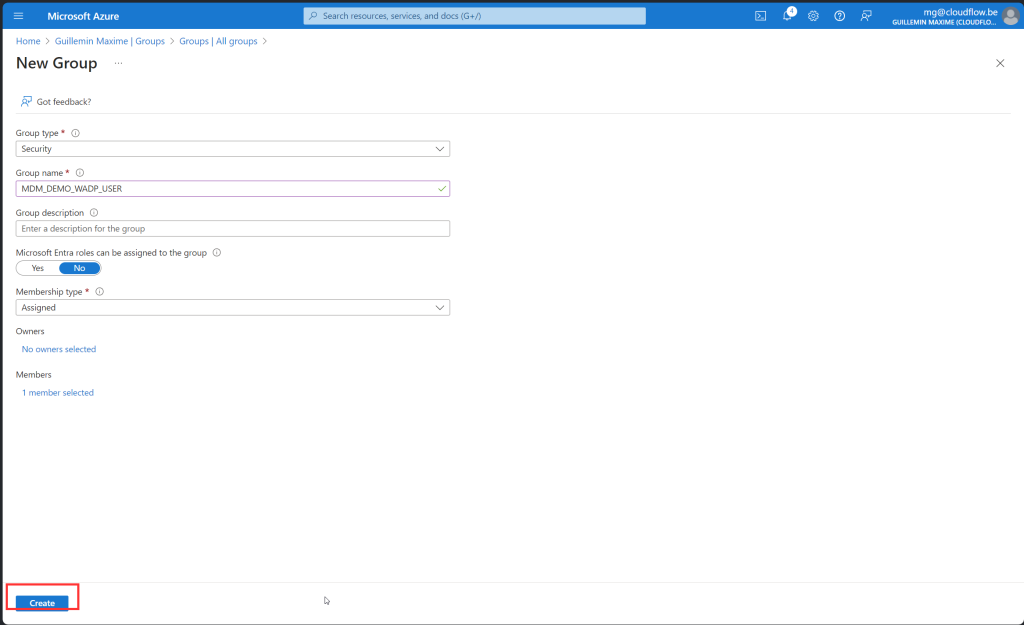
Assign Device group
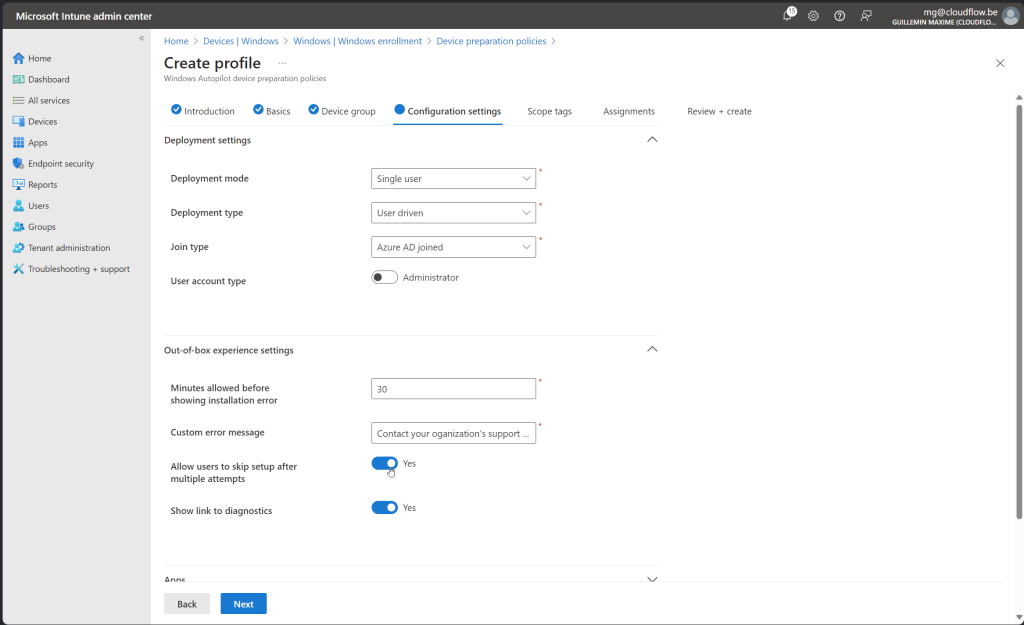
Assign your Configuration Profiles, Compliance policies, scripts and Applications to the Devices
- The device group is selected in the Windows Autopilot device preparation profile.
- Only applications and PowerShell scripts selected in the Windows Autopilot device preparation profile are deployed during OOBE. Any additional applications or PowerShell scripts assigned to the device group will be deployed after the Windows Autopilot device preparation deployment is complete.
- For policies, Windows Autopilot device preparation syncs any policies assigned to the device group. However, Windows Autopilot device preparation doesn’t track if the policies are applied during the deployment. The policies might be applied either during the deployment or after the deployment is complete.
Create WADP
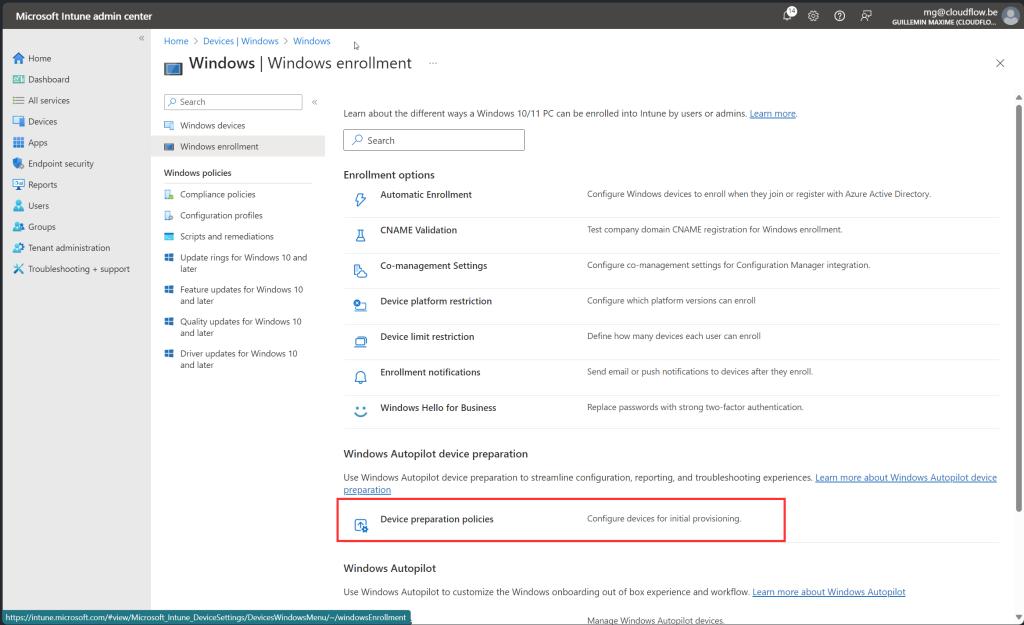
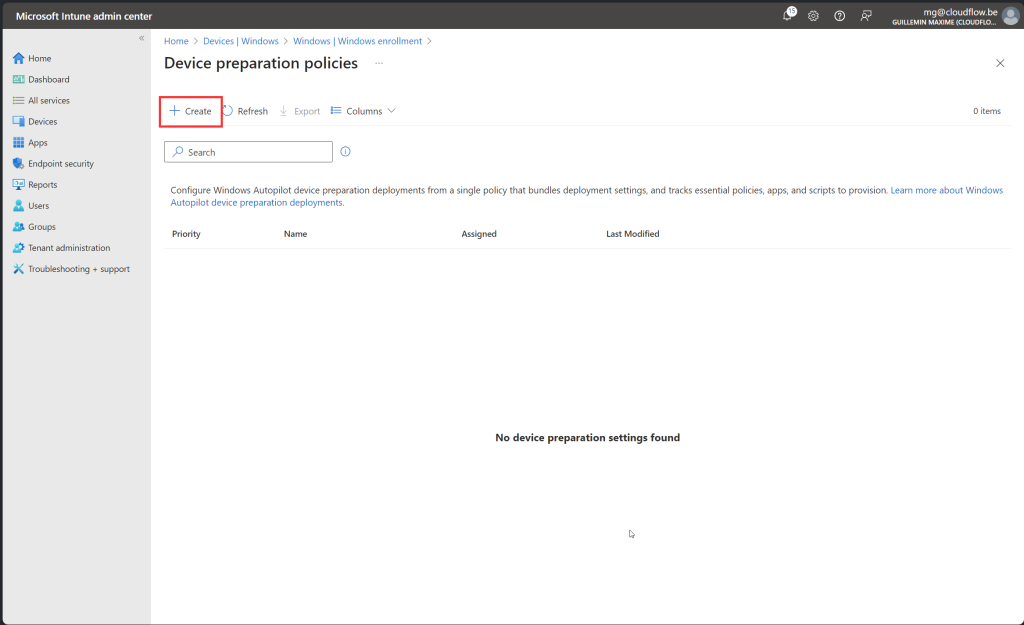
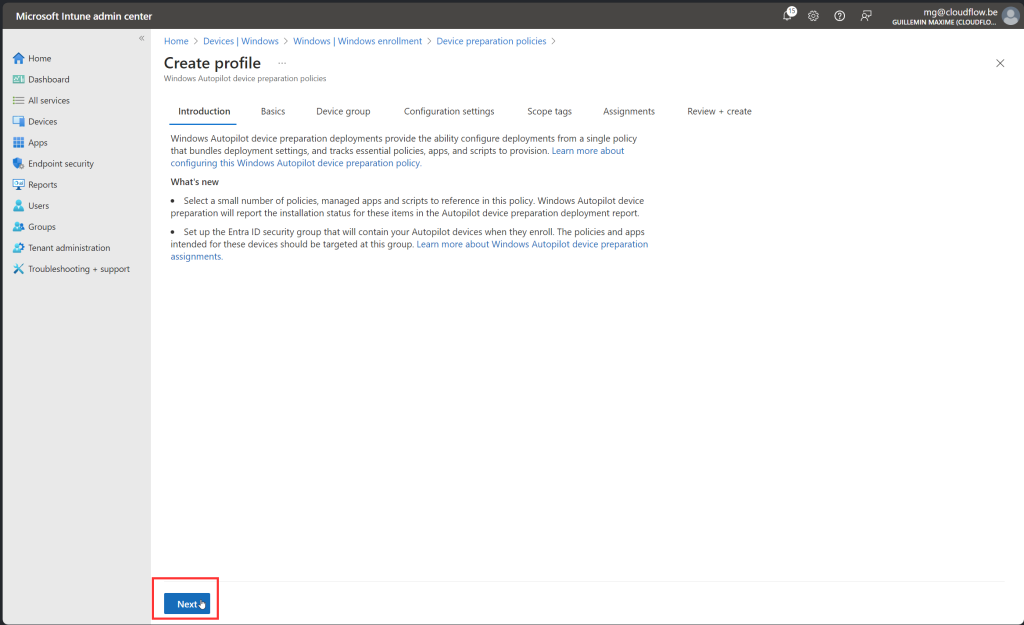
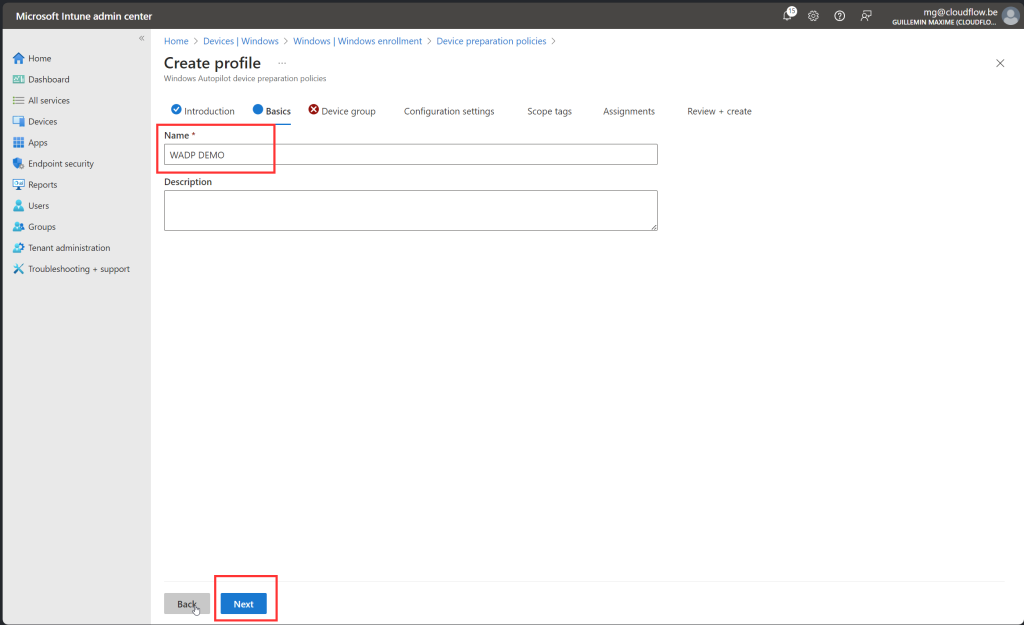
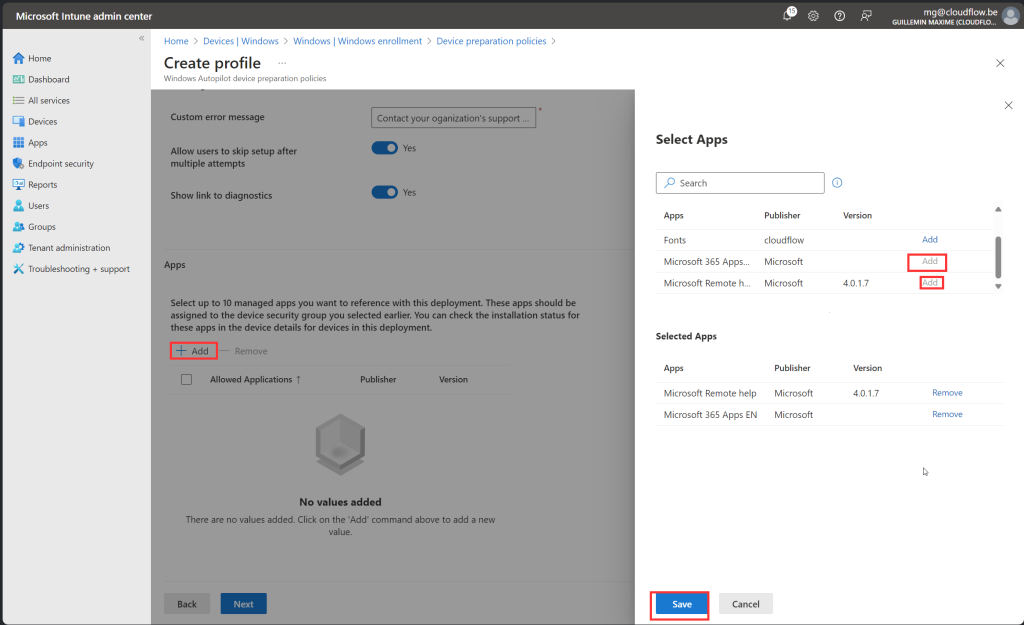
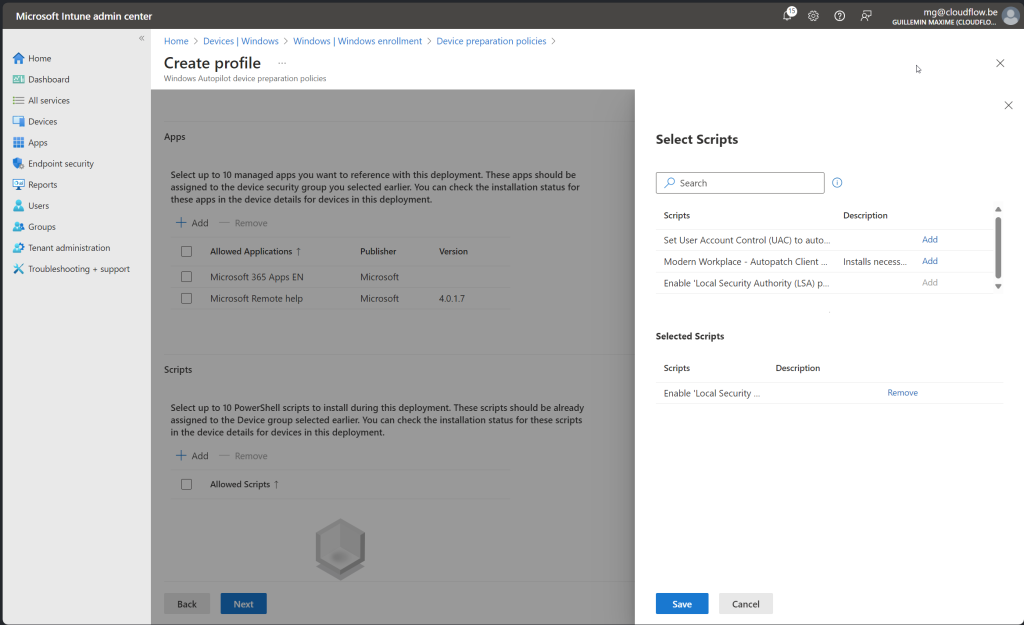
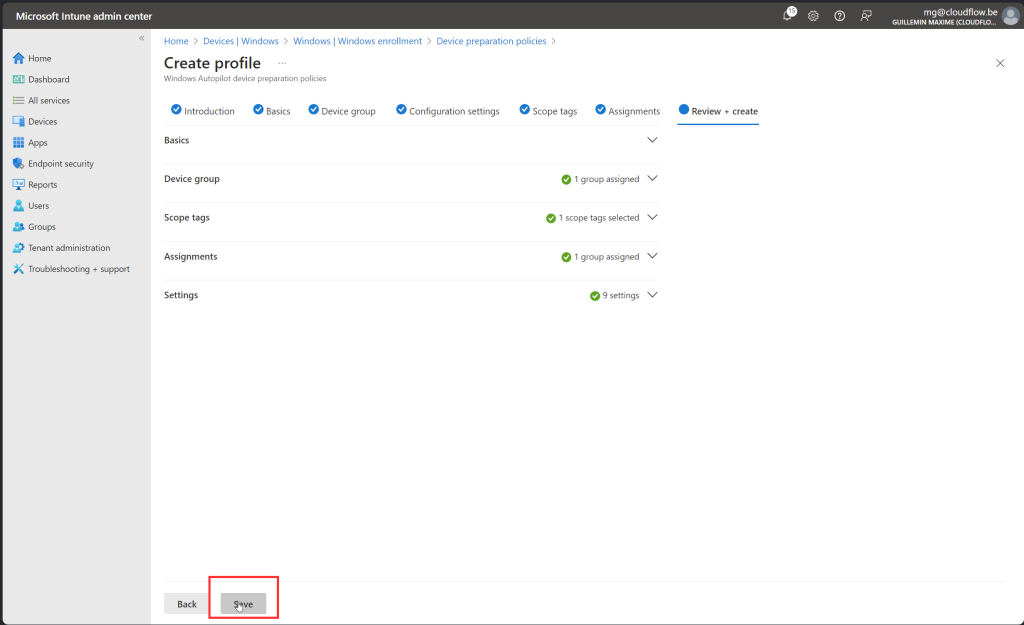
Lets Try it !
Device enrollment
Before you Try it make sure your device meets the prerequisites
- Minimum OS Version
- Supported OS Editions
- Windows 11 Pro
- Windows 11 Pro Education
- Windows 11 Pro for Workstations
- Windows 11 Enterprise
- Windows 11 Education
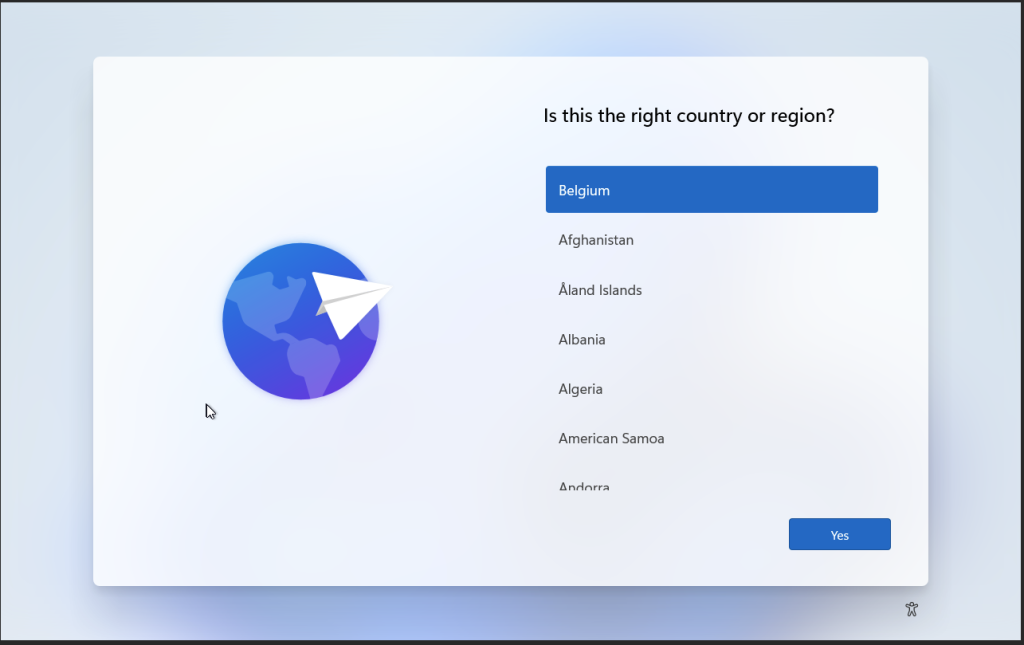
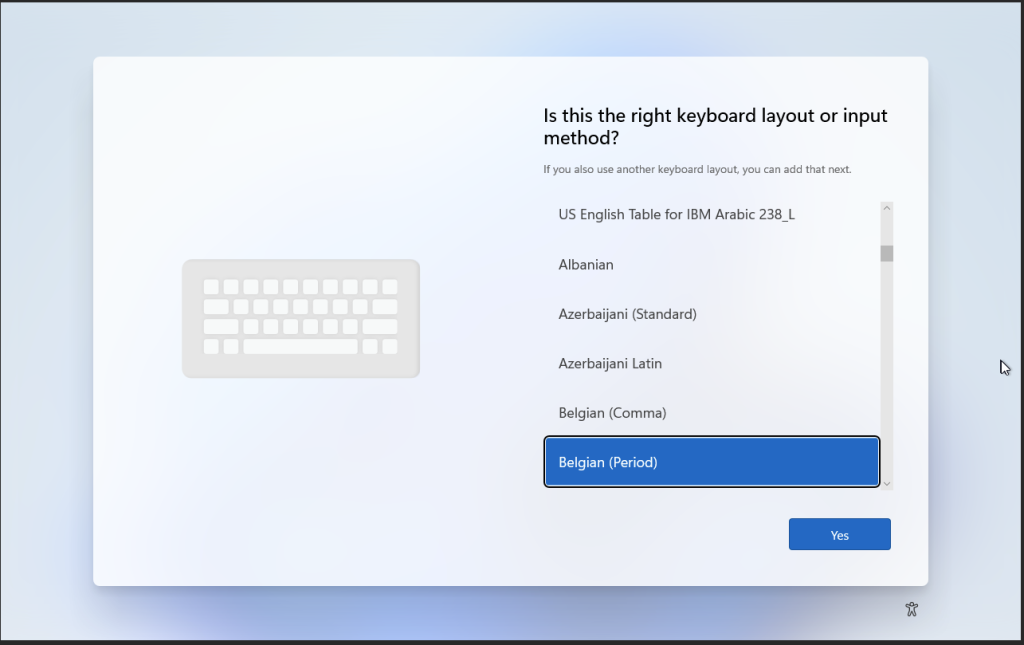

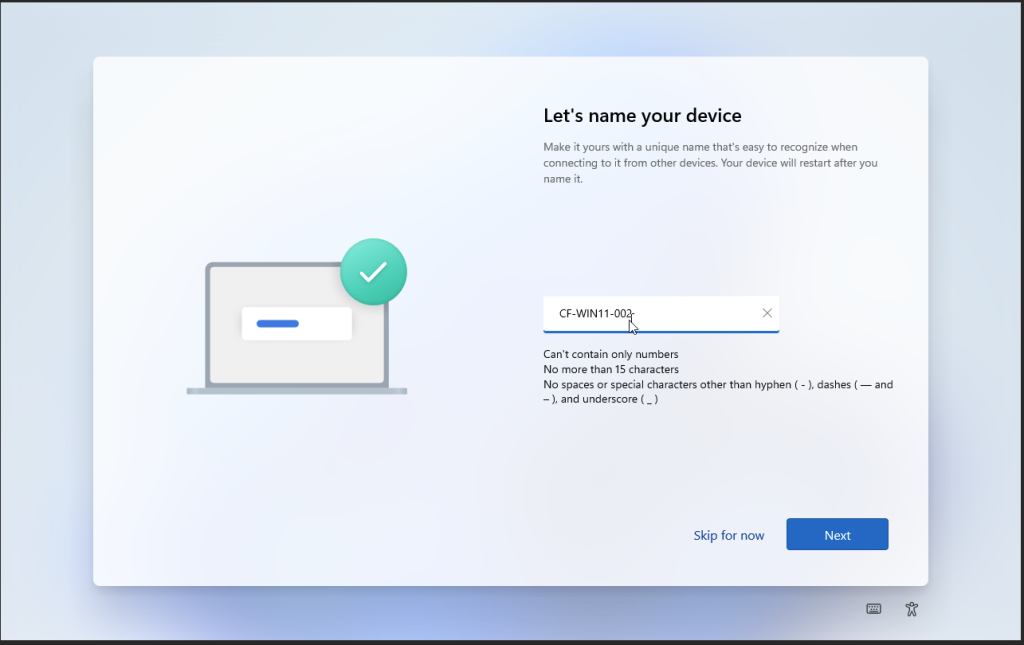
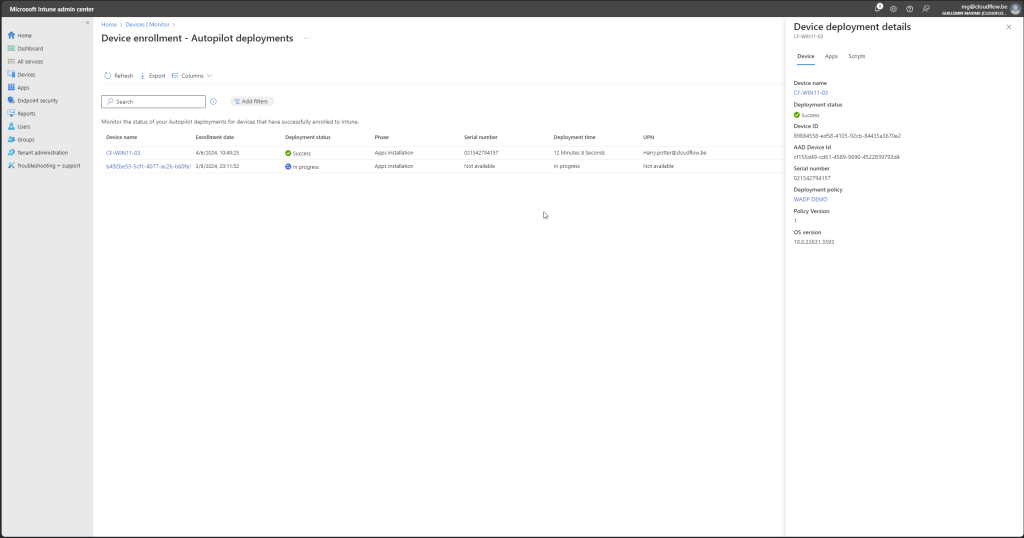
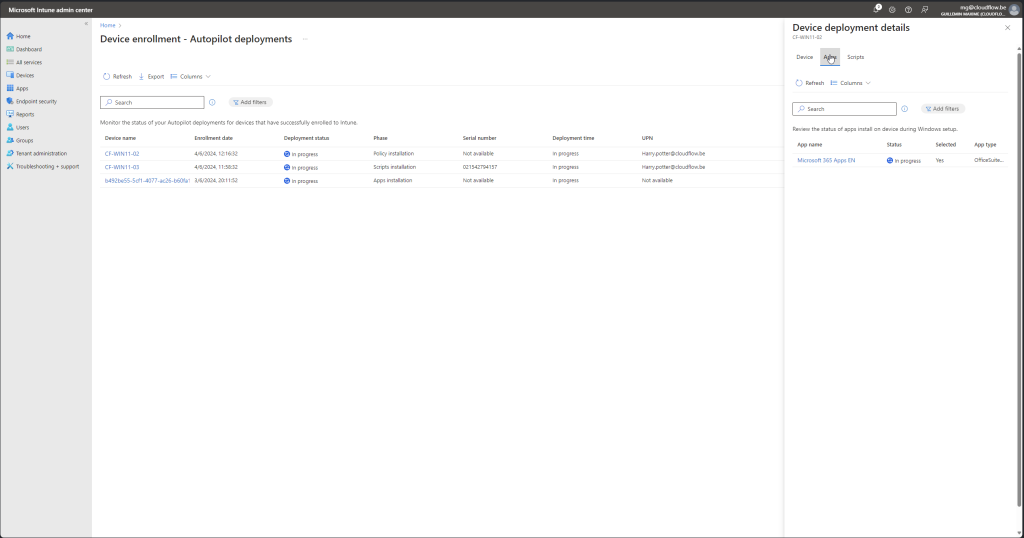
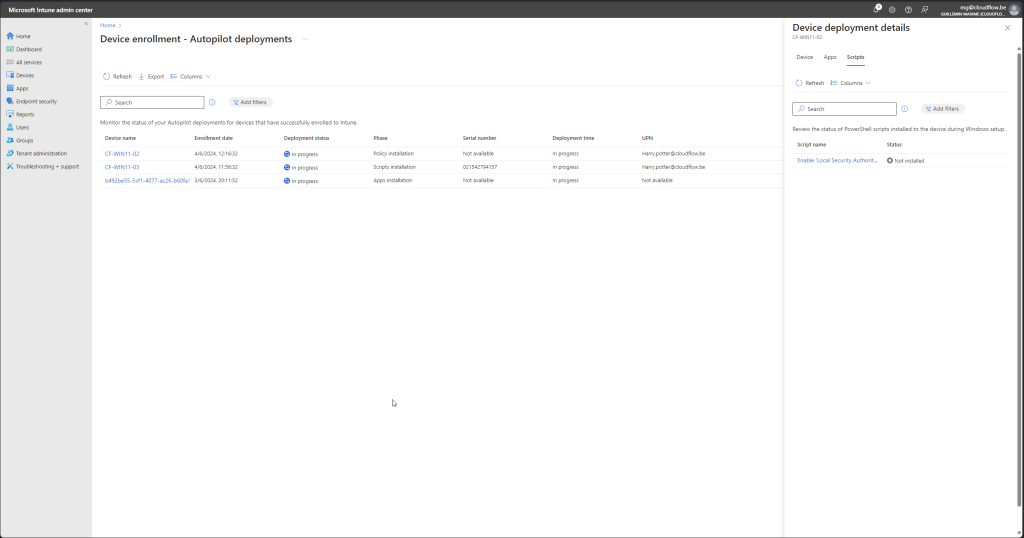
Status page
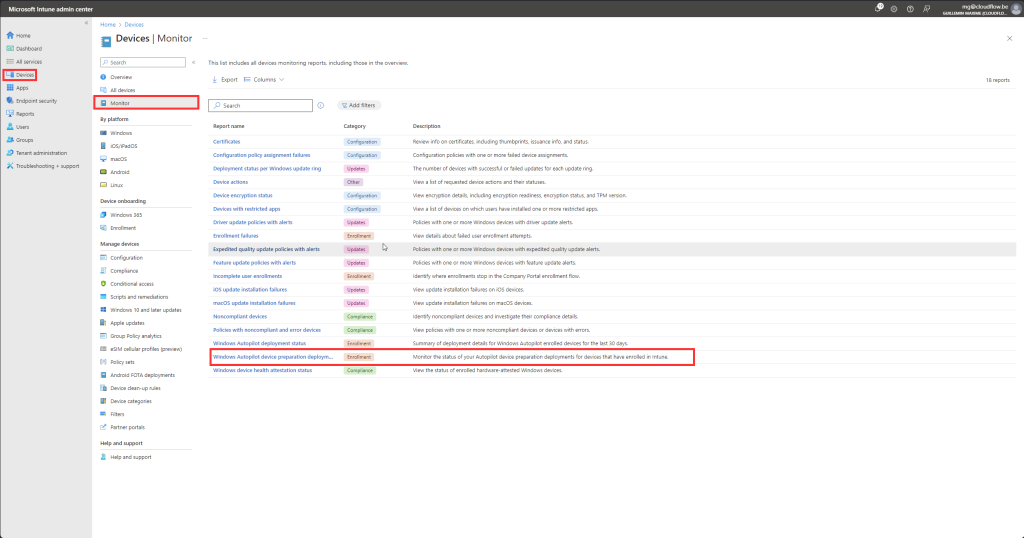
Go to https://intune.microsoft.com > Devices > Monitor > Windows Autopilot device preparation deployment
With the WADP status pages you should be able to track you deployments live and see where it fails if you have any issues. Compared to the autopilot this is a great feature to have where you only got some cryptic error. it still needs some work but its a good start.
Issues
- Status pages keeps showing in progress when deployment is done
- Status page was not always available during the deployment
- The url was not shown on the endpoint during the deployment while specified in WADP Profile
Conclusion
It’s a lot easier and involves much less hassle to enroll a device, making it a good start. However, there are still some shortcomings at the moment. In my personal testing, I encountered some failed deployments, but when running the process a second time without any changes to the configuration, it succeeded. I also experienced issues with logging in after a full password-less rollout.
Options to choose which configuration policies are applied during OOBE are needed. Some configuration policies, like delivery optimization policies, can result in delays in the rollout. Additionally, the ability to hide the EULA and privacy settings is missing, as well as a device name template.
Overall, I think it’s a good start, but I’m hoping to see more improvements, including addressing the obvious missing items mentioned above. For now, I will be sticking with traditional Windows Autopilot because it is not yet mature enough, and there are also some things it will never be able to do, like preventing end users from configuring it with the wrong account. Additionally, the time it takes to update the device to the supported version can be used to extract the hardware hash and enroll it via Autopilot. However, I do hope the live status page comes to Autopilot once it’s more mature and stable.
If you have any Question or Things you want me to test let me know and ill get back to you 😉
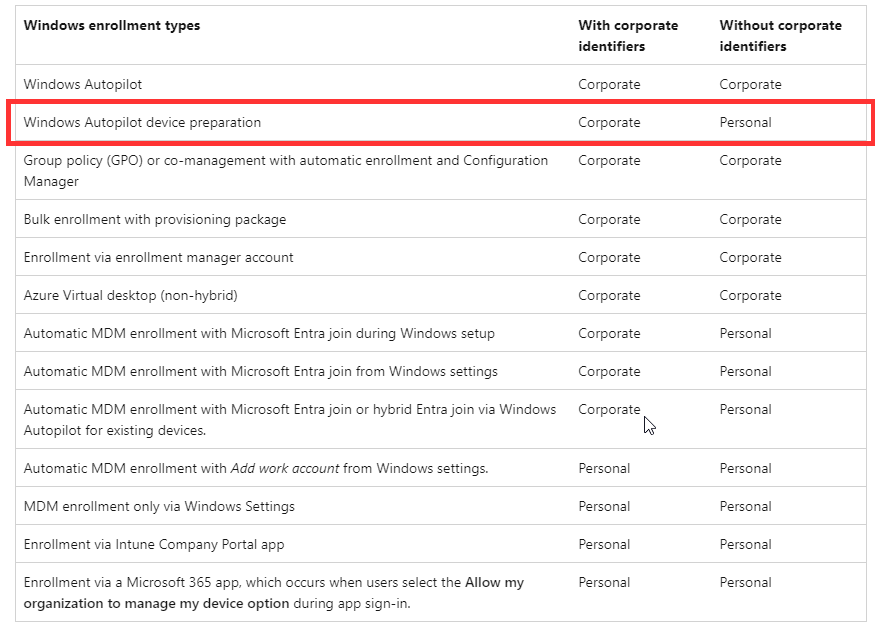
Update Corporate / Personal Owned devices
I had the question: how will Intune label the device as corporate or personal owned? If you don’t make use of corporate identifiers, the device will always enroll as a corporate device. However, by using corporate identifiers, only devices listed in there will be marked as corporate, while all others will be marked as personal owned.
How to set it up
Go to https://intune.microsoft.com > Devices > Enrollement > Corporate Device identifiers > Add
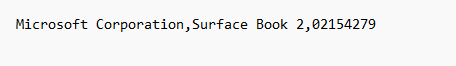
Create a CSV And upload it. it should look somthing like this.
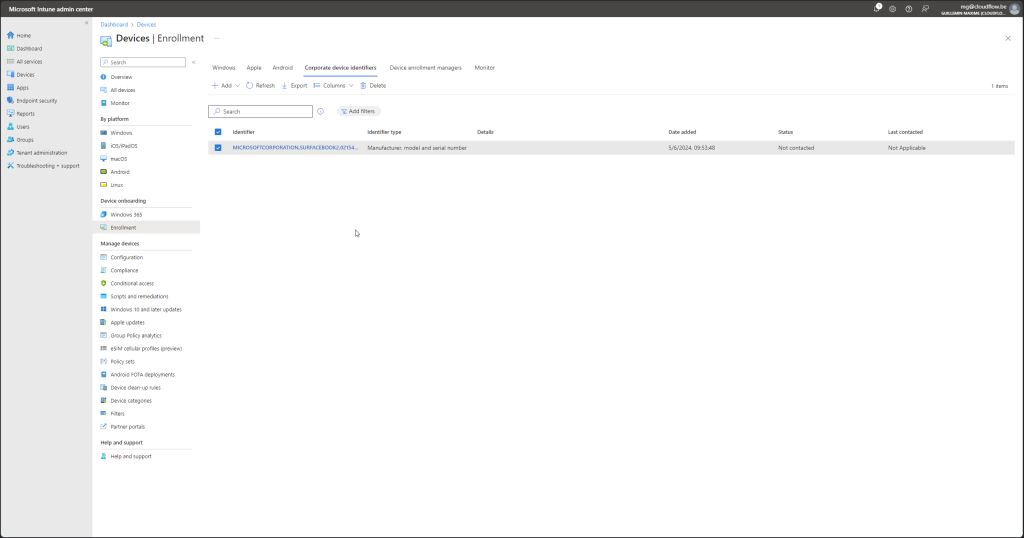
And now if you rollout a new device that is not listed here will be added as a personal device and the devices here will be company owned devices.






Thank you! You just saved me about 8 hours!
I do assume that by tomorrow, off the pages in Azure will be rearranged and I will feel like a crazy person that once knew reality.
No problem glad to be of help
Hi, every time I add the device group and save, next time I go into my policy it shows 0 groups assigned.
The group has the service principal added as the owner.
Any ideas?
Hey James
Have you tried crating a new profile and trying it again.
if the service principal was not assigned you should get an error.
You could also try doing it manually via graph api call.
i have a blog post on that how you can do it.
https://cloudflow.be/windows-autopilot-device-perpetration-with-graph-api/
with kind regards
Maxime
Thanks for the guidance…
I am stuck! I followed your guide and everything is configured as described here. When I try to register a device I always get the following error (only if I set the device restriction to “corporate only”)
Details
This device cannot be registered as a personal device while the platform is locked in Device Type Restrictions.
Recommended steps
The user must use a different platform for the personal device to be registered. If it is an enterprise device, make sure that the user is registering correctly and that the device has been added to the list of enterprise device identifiers, if necessary. You can check personal platform restrictions under Device Enrollment > Enrollment Restrictions > Choose a Restriction > Configure Platforms.
I loaded the CSV with the enterprise device identifiers on the tenant and I see something like this: DELLINC,LATITUTE5591, is this correct?
Also, the device, is not in the list of hashes loaded with the classic autopilot system.
Where am I going wrong? I really don’t understand where the problem is. It is as if it does not recognize the test device as corporate.
I solved the issue! the computer was missing a microsoft update recommended in the deployment guide
I’m not sure exactly why but this web site is loading incredibly slow for me. Is anyone else having this issue or is it a issue on my end? I’ll check back later and see if the problem still exists.
Hey
I’m working on it 😉 hopefully the new site live this month.